![]() A physical security information system, also known as PSIM, requires a platform that unites and connects security-related physical components and allows monitoring and controlling of every element through a powerful interface within a framework built on extensibility and complete integration.
A physical security information system, also known as PSIM, requires a platform that unites and connects security-related physical components and allows monitoring and controlling of every element through a powerful interface within a framework built on extensibility and complete integration.
LightHouse™ seamlessly unifies every component of a user's security system, providing comprehensive and total control within a single, intuitive interface. The PSIM system supports virtually any part, sub-system, or third-party security product. It has been successfully deployed in federal, military, and energy utility installations as well as municipal, educational, healthcare, and commercial sites.
LightHouse™ will continue to meet your organization's security needs, providing our updated PSIM system as technology evolves and your requirements change.
When all the data generated by every device in every facility throughout your organization comes together within a unified and well-organized interface, tracking, controlling, responding to events, and maintaining records becomes much more straightforward. That's the power of unification — and a distinct advantage of the LightHouse™ PSIM platform.
LightHouse™ is designed and programmed to accommodate virtually any device or sub-system imaginable within your security system and throughout your entire enterprise. Whether alarms, doors, intercoms, cameras, building management devices, lighting controls, telephones, network devices, or software inputs, LightHouse™ PSIM can support virtually any electronic device or system operating on any protocol, giving you the highest possible level of unification and control.
This unification and control capability is compelling in organizations where multiple systems interact and share information, such as IT, personnel management, network security, HVAC, and manufacturing systems. Each security device or sub-system is connected to the overall system through a "Portal," Devices with similar characteristics can be grouped for easier management.
LightHouse™ also takes unification beyond the system level. For example, if you have multiple LightHouse™ controlled security systems operating at separate facilities or campuses, a user with the proper permissions can connect to any or all of them simultaneously. Users can also control and manage multiple systems anywhere via any authorized workstation.
Everything else is irrelevant if the security system is vulnerable to abuse, eavesdropping, or other unauthorized activities. That's why LightHouse™ uses a robust collection of superior authentication and encryption methods to ensure your system's security.
 The LightHouse™ Server lets you assign each user several profiles (user roles) that determine which functions the user can perform, which devices the user can access, and even the hours during which the user is authorized to operate the system. You can also use user group functionality to assign or change permissions for any number of users at once.
The LightHouse™ Server lets you assign each user several profiles (user roles) that determine which functions the user can perform, which devices the user can access, and even the hours during which the user is authorized to operate the system. You can also use user group functionality to assign or change permissions for any number of users at once.
The LightHouse™ Server manages client connections, each authorized through an assigned user profile with corresponding permissions. This role-based access control (RBAC) is the heart of user permissions.
All communications between the client and the LightHouse™ Server are authenticated and encrypted using the latest, most secure algorithms. The LightHouse™ Platform complies with the FIPS 140-2 Security Requirements for Cryptographic Modules defined in that publication.

The scheduling functionality of LightHouse™ can be used to set automatic actions like turning on lights or bypassing specific alarms. The schedules you create and the numbers or types of devices controlled by the programs are virtually limitless. For example, the actions can be scheduled as repeating events to occur daily or weekly — or as one-time events at any date and time the user chooses, even years in advance.
With the development of a global marketplace, many organizations require a system that can accommodate globalization in a secure and logically managed environment. LightHouse™ provides time zone reconciliation and management so that users, devices, schedules, events, incidents, and reporting can all be governed and logically presented to the user. Therefore, there is no need for an operator to calculate or decipher time zone differentials on the system, as LightHouse™ manages this for you.
LightHouse™ also supports rules-based management with plugin components. These specialized software components enable customized functionality in your system, whereby an event or combination of events can trigger an action in another part of the system.
The LightHouse™ Unified Security Management Platform collects, analyzes, and unifies all available information from physical security devices and systems, network monitoring, and other software packages into a comprehensive view for operator management and control. It provides situational awareness with video and audio (enabling call-on-incident and listen-in capability), real-time device status, advanced incident management, and conditional behavior functionality.
The LightHouse™ System Manager is the central server component for any LightHouse™ system. It securely manages user permissions, client connections, device/object linking, and timed events. LightHouse™ is available as a software-only package or as server hardware with pre-installed software and is modular, allowing easy integration into other systems in the future. In addition, it can support an infinite number of unique layout views and dashboards for unlimited users.
The LightHouse™ System Manager software supports core capabilities augmented by portals and optional software modules and supervises administrator and user rights and permissions. Each user is assigned one or more profiles (roles), encompassing permissions for screen layouts (dashboards), schedules, workstation permissions, and device interactions. A flexible plugin-oriented system is utilized for user authentication, supporting many methods. Client and system manager communications are authenticated, encrypted, and FIPS 140-2 compliant.
The LightHouse™ System Manager supports both physical and virtual devices within the limitations of the systems integrated and associated hardware. Devices may be related to others to form a device group for monitoring and control purposes. User groups may be created to generate standard profiles, properties, rights, and privileges. It also can handle control- and layout-based display synchronization across multiple clients via a shared dashboard or layout. Clients support facility, location, and object mapping, including displaying situational awareness information on rendered drawings, complete with state-specific icons of each monitored component.
The system can support unlimited conditional behaviors, allowing it to automatically perform actions based on the device, system state, and time when a given set of circumstances occur. Dependent behaviors can trigger complex commands (macros), such as device commands, software users, and third-party notifications. The System Administrator defines macros.
Central to the unified security system is unified logging and reporting capabilities. LightHouse™ logs all system and user actions for later review, and reports are available for activities and states, devices, and incidents. They can also be associated with video recordings and cardholder access.
Portals are software components that provide the LightHouse™ System Manager with specific functionality and capabilities, such as controlling and monitoring video, intercoms, and access control systems, among many others. Network Harbor works with manufacturers to produce portals that support virtually any electronic system using any communication format, including IP-based, serial, or proprietary protocols. The LightHouse™ System Manager's core capabilities are augmented by plugin software modules, which can meet or exceed FERC (Federal Energy Regulatory Commission) standards. For more information on our portal solutions, contact us.
The LightHouse™ Graphical Client Workstation is highly intuitive, enabling users to navigate and control their security system easily, quickly, and precisely. Each device can be represented by an icon, hotspot, or perimeter on any map format defined in the LightHouse™ map display packages.
The platform's basic map display package supports most standard formats, including AutoCAD® (.dwg and .dfx, including 3D), and file formats, such as .bmp, .jpg, .gif, and .tif. Optional packages support various 2D and 3D modeling formats and GIS maps utilizing data from online servers or offline resources. These include real-time data to track entities like storms, vehicles, assets, or people. LightHouse™ can support new graphics formats as they are developed and can add features to support the needs of your application.
LightHouse™ uses advanced icon capabilities (through Icon Plugins) to help users visualize the security system and all its components from any perspective or zoom level. Available icon styles include vector-based icons that scale as the user zooms in and out, transparent, semi-transparent hotspots, and perimeters (e.g., fence segments).
An extensive library of icons is provided, and an icon editor for each Icon Plugin lets you create and edit the type of icon best suited to your system. An extensive library of controls, such as status lists, map windows, video windows, and transaction lists, are provided to meet the unique requirements of any user. In addition, custom controls can be provided. Screen layouts can also be configured as desired on multiple monitors.
Using a mouse, touchscreen, or keyboard, the user can select the device from a sorted or searched list, drag and drop onto the map control for the auto call of an assigned map, or mouse over the icon to bring up a form indicating the device status or other information. A simple click accesses the controls specific to the device.
To view a live video feed from any camera, including a camera directly associated with a particular door, reader intercom, or relay, the user drags the corresponding object to a video display window or double clicks to pull the video to display or does a video call-up with icon flyover.
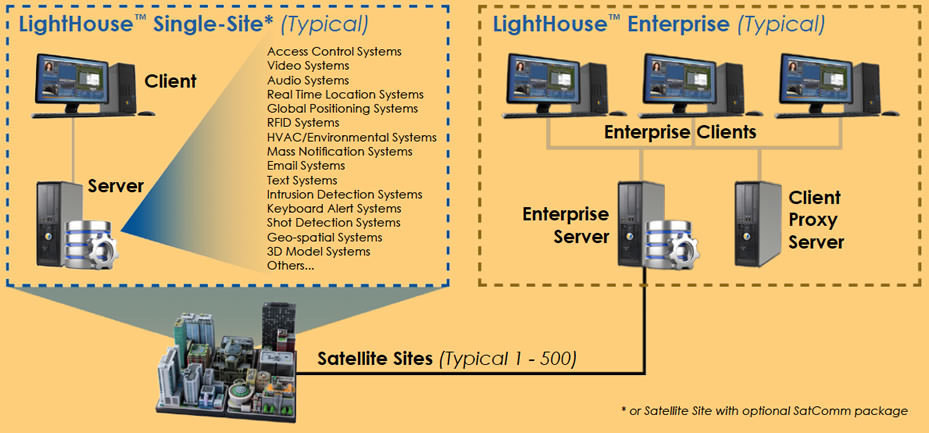
The LightHouse™ platform also allows Enterprise-level operations to monitor and control multiple "satellite" standalone sites with Enterprise communication packages concurrently as a centralized operation. LightHouse™ Enterprise supports the continued operations of satellite systems offline from the Enterprise server. In addition, it includes multi-site aggregate report functions, facilitating simultaneous cooperative management of alarms and incidents between local and enterprise users (see diagram below left).

Rather than just informing the operator of incidents like alarms, LightHouse™ offers advanced incident management capabilities that allow the operator to acknowledge or silence the alarm while keeping the incident active. Operator activities and devices associated with the incident are time-stamped and logged. Detailed incident reports can be accessed at any time, and additional information can be added without compromising the integrity of the previous content.
Users can access any event by calling up an incident list, clicking on a graphical object that corresponds to the event, or selecting the event from a transactions window. Predefined entries are available to expedite reporting but can always be overridden. When the incident is resolved, it can be closed, and the associated audio and video are saved with the report. Users with the proper permissions can reopen events for review and add data anytime.
In addition to standard incident management with user-defined drop-down lists of preprogrammed responses, structured incidents are also provided for assigning SOPs (Standard Operating Procedures) to any event. Based on operator response, these can be configured and assigned to stepped procedures and branched operations. In addition, structured incidents have no limitation on the number of steps and techniques that can be configured.
The LightHouse™ System Manager supports many critical functions essential to the unified platform working with your other integrated solutions, like gears in a well-oiled machine.

Contact us today to see a live demonstration of LightHouse™, receive more information about this unique solution, ask about our related hardware units, learn more about our other LightHouse™ services and software, or request a quote.